ESI INENDI is a unique solution geared towards the Analysis and the Investigation of large volumes of logs.
Cyber Risk Control
Continuous Cyber Risk Control is a security practice gaining value amongst security practitioners.
One ESI INENDI customer was facing a classical situation most large companies have to deal with; how confident can we be in the efficiency of our SOC & CERT infrastructure and its ability to control our exposition to Cyber Risk?
Overtime, this global company had invested in a highly equipped security infrastructure, outsourced its SOC to a major player in that domain, hired talented people to drive its CERT and was educating the top management on the importance of Cyber Security. They even reached a point in time where the KPIs of this security machinery were pretty good: small number of major attacks, reasonable response time to identified incidents, etc.
Motivated by their drive to continuously improving their Cyber Defense, they asked INENDI to execute a Deep Log Investigation on a large perimeter: 3 months of network activity, over all EMEA offices (+100K machines).
The goals of this investigation were prioritized to target weak signals and important events that had not been detected by the security equipment or that had not been identified as important at the SOC & CERT level.
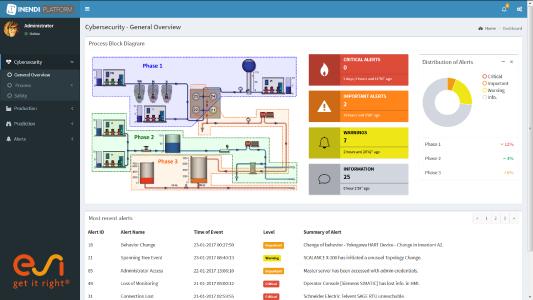
ESI INENDI's search revealed numerous security breaches left unseen or unmanaged, including advanced botnets. Others related to malware targeting specific populations of employees of the company. Many dangerous, yet unknown, users’ behaviors were spotted as opening the door to malicious activities and were detailed in a way that allowed their integration in the cyber defense systems.
Even with a large and complex network, ESI INENDI proved that Deep Log Investigation is an efficient method for producing the “fresh” information needed to continuously control how a company is exposed to Cyber Risk.
Master Big Data, Weak signals and APTs
As everyone admits today, the challenge of Cyber Security is to be able to identify weak signals and unknown threats in that vast amount of information available inside (i.e. in the company’s IT system) and outside (through various sources of knowledge and threat intelligence).
Obviously, it looks like a typical Big Data situation. Hence, we all naturally tend to look for solutions similar to the ones that can be found in other domains where Big Data reigns.
Like a search engine, so helpful in our daily use of the Internet, it looks like it is a valid answer to the Big Data issue we have in Cyber Security!
The same unconscious transfer happens with dashboards that are so helpful in Finance, Administration, Management, etc: it also looks like an appropriate answer to our Big Data issue.
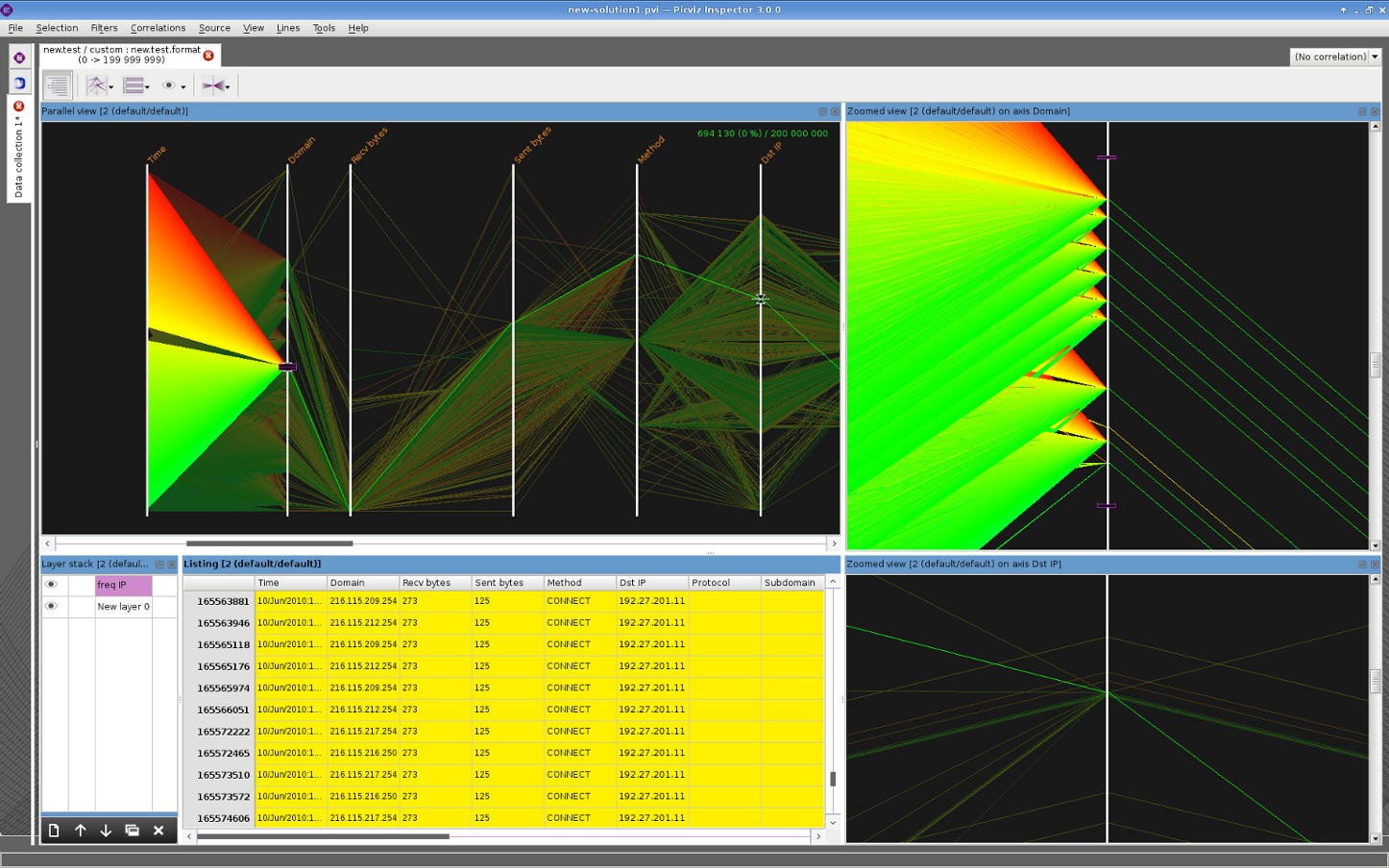
There is however a huge limitation in the efficiency of the classical Big Data tools in Cyber Security. We are looking at threats and hackers who will adapt and evolve to take advantage of the particularities of your IT system and of its users. We are not talking about a generic, standardized threat. We are talking about a Cyber weapon that will specialize itself to target your positions on your battle field.
To handle such a threat, there is a pragmatic approach that is based on a very old advice to be found in Sun Tzu’s famous book named The Art of War. In this book, Sun Tzu promotes some principles and some concepts that structure good strategy to win battles. One of these principles states:
"Know the enemy and know yourself; in a hundred battles, you will never be in peril”
Sun Tzu
One concept associated to that principle is to be aware of the “terrain” where the battle is likely to take place. This immediately applies to Cyber Security, where observation and study of the information “terrain” are a necessity.
By regularly exploring its IT logs, one of our customers (in the chemical industry) got an intimate knowledge of how his network, services and users behave. Later, this knowledge and the ability of INENDI Inspector to ease the detection of anomalies, made possible the identification of a subtle fraud that was taking place through one of its product-accounting servers in the production area.
For the same reasons, another customer could locate very quickly which machine in his networks had been infected after a successful DNS-amplification attack had happened on one of its servers, hiding injection requests to gain root access. The standard rules of the IDS were not capable of detecting the activity of the newly infected machines.
INENDI Inspector will help you get a deep knowledge of your IT system and master this Cyber terrain before your attackers.